Navigating the new era of AI and deepfake-driven fraud in financial services

Key takeaways
- Fraud is becoming more sophisticated rather than simply more frequent, with AI and deepfakes enabling targeted attacks that exploit trust and legitimate workflows.
- Disconnected fraud, AML and identity systems make it harder to spot coordinated activity that spans channels and time.
- Automation scales detection, but human experts are critical for judgment, escalation and regulatory confidence in complex cases.
- Connecting signals across systems and teams is more effective than adding isolated tools.
- Augmenting internal teams with specialized partners, like TELUS Digital, can help organizations adapt without rebuilding programs.
The call looked routine at first. A senior finance director at a multinational firm joined a video meeting with what appeared to be her company’s CFO and several colleagues she had worked with for years. Everyone looked and sounded exactly like themselves, and she didn’t realize it wasn’t real until it was too late.
The entire meeting was a coordinated deepfake. Criminals had reconstructed the team using publicly available video and audio. Together, these synthetic “coworkers” urged her to authorize a number of confidential multimillion-dollar transfers. By the time the deception was uncovered, more than approximately $25.6 million USD had been wired out of the company’s accounts.
While deepfake attacks can target any enterprise, financial services organizations face a uniquely high-stakes version of the threat. Banking, payments, insurance and capital markets rely on trusted digital identities and fast-moving approval processes across onboarding, transactions, lending and claims. As AI-driven deception becomes more advanced, those same systems create opportunities for fraud to move quickly and quietly through legitimate channels.
This reflects a broader shift in how fraud is executed. According to Sumsub’s Identity Fraud Report 2025-2026, the real story isn’t a rise in the volume of fraud, but in its sophistication. Advanced attacks involving deepfakes, AI-generated identities and multilayered social engineering have increased 180% year-over-year, marking what Sumsub calls “The Sophistication Shift.”
“The Sophistication Shift marks a turning point, as businesses now face challenges related to their velocity and the speed at which they can detect threats and adapt,” wrote Andrew Sever, CEO at Sumsub. “The next frontier of fraud prevention will belong to those who can unite human insight, data intelligence and AI precision to build trust at scale."
For financial institutions, this shift overturns long-standing assumptions about how fraud behaves and how it can be detected. Attackers can fabricate identities, clone employees, impersonate customers and manipulate trusted communication channels with a level of realism that overwhelms human intuition and evades traditional controls.
The result is a new era of deception for financial services organizations — one that threatens operational integrity, regulatory compliance and customer trust all at the same time.
Inside the new fraud playbook: What threats are financial leaders seeing today?
Increasingly, AI is being used to exploit the very foundations of modern financial services: trusted identities, rapid approvals and seamless digital interactions. Rather than relying on overt system breaches, today’s attacks are subtle, coordinated and designed to blend into normal decision-making flows.
In the sections that follow, we examine the AI-enabled threats financial services leaders are confronting today, the challenges slowing effective response and how institutions are adapting their defenses in practice.
AI-enhanced deepfake social engineering
Deepfake social engineering represents one of the most destabilizing shifts in modern fraud because it targets the human layer of financial decision-making rather than technical controls alone. Attackers can now use AI to convincingly replicate executives, employees and trusted counterparties across video, voice and messaging channels.
In financial services, where approvals are often time-sensitive and authority-driven, these attacks are particularly effective. A request that appears to come from a trusted leader, delivered through what looks like a legitimate internal meeting, can short-circuit traditional safeguards designed for email fraud or credential theft. The result is not just unauthorized transactions, but a breakdown of confidence in the channels financial institutions depend on — undermining customer trust and putting brand reputation at risk when fraud plays out in highly visible ways.
“The challenge with deepfakes isn’t that institutions lack controls, it’s that many of those controls were designed for a world where seeing and hearing were reliable signals of trust,” said Carolyn Fox, director of trust and safety at TELUS Digital. “Today, leaders have to assume deception can look perfectly legitimate and design approval workflows that don’t rely on any single channel as proof.”
Leading financial institutions are responding by rethinking how trust is validated in high-risk moments. Rather than relying on a single signal — whether a video call, a voice match or a login credential — organizations are designing layered decision paths that assume any one channel can be compromised. This includes separating identity from authority, distributing approvals across people and systems, and continuously assessing behavioral context before sensitive actions are completed. Importantly, these controls are applied dynamically, introducing friction only when risk signals justify it. This allows institutions to secure high-impact decisions while preserving speed and experience for legitimate customer activity.
Just as important, many institutions recognize that executing these controls at scale requires more than internal capacity alone. Deepfake-driven attacks are often time-pressured, high-value and operationally complex, making speed, consistency and specialized judgment critical. Augmenting in-house teams with dedicated fraud operations via outsourcing can strengthen decisioning precisely where the financial stakes are highest.
For example, in one engagement, a global financial institution partnered with TELUS Digital to strengthen protections across the customer journey. As part of this effort, our team of expert fraud specialists helped implement a high-dollar restriction and approval matrix, ensuring elevated scrutiny for the most financially sensitive actions. This approach exceeded the client's fraud-detection quality target of 85% (90.8% achieved) while driving significant cost recovery through chargebacks and re-billing before regulatory deadlines.
Synthetic identity fraud and AI-driven document forgery
Synthetic identity fraud has moved beyond isolated onboarding failures and into a systemic risk for financial institutions. By blending real personal data with fabricated attributes and AI-generated documentation, fraudsters can create identities that can withstand traditional Know Your Customer (KYC), Know Your Business (KYB) and onboarding scrutiny not just once, but repeatedly over time.
What makes these attacks particularly destabilizing is not just their realism, but their persistence. Once admitted, synthetic identities can behave like legitimate customers for extended periods, quietly accumulating credit exposure, enabling money movement or masking downstream money laundering activity before triggering suspicion.
Because these identities often enter through high-volume, high-trust workflows such as onboarding, credit origination and business verification, the impact compounds quickly, and financial loss is only part of the equation. Regulatory exposure and erosion of confidence in digital onboarding models raise deeper questions about how trust is established and maintained.
In response, leading institutions are rethinking identity as a continuous risk signal rather than a one-time checkpoint. That means pairing advanced document forensics with selective liveness checks, correlating identity signals across systems and channels, and using behavioral and device intelligence to evaluate how an identity behaves over time. Human judgment remains essential but increasingly reserved for the highest-risk edge cases where automation alone cannot provide sufficient confidence.
The value of scalable, multilingual verification is illustrated by a leading global payments and compliance technology provider that partnered with TELUS Digital to strengthen its KYC operations amid surging verification demand. To support growth without compromising accuracy or compliance, we deployed a specialized team supported by Fuel iX™ — our award-winning generative AI (GenAI) engine — to automate and orchestrate core KYC workflows, including document intake, triage and case routing. This AI-driven foundation enabled our teams to focus on back-office KYC activities such as identity verification, card issuance reviews, line-of-business validations and enterprise security assessments.
The engagement delivered strong operational outcomes that exceeded benchmarks, with a 96% quality assurance score for KYC inquiries (over 100 resolved per hour).
AI-driven credential stuffing and intelligent bot attacks
Credential-based attacks are not new. What is new is how GenAI has transformed their scale, precision and resilience. Attackers no longer rely on blunt, high-volume login attempts that trigger obvious alarms. Instead, AI-driven bots now behave like legitimate users, adapting in real time, rotating devices and mimicking natural interaction patterns to probe defenses quietly and persistently.
“Credential abuse is no longer just a login problem. It has become the entry point to broader account-takeover (ATO) campaigns, enabling downstream fraud across payments, profile changes and privileged access,” said Ljubiša Velikić, vice president of trust and safety at TELUS Digital. “When attacks are adaptive by design and indistinguishable from real customer behavior, traditional rate-limiting, static rules and password-centric controls simply can’t keep up — which is why detection often happens only after financial loss or customer impact has already occurred.”
To stay ahead, institutions are moving away from perimeter-based defenses toward controls that continuously assess risk throughout the session lifecycle. Effective approaches include risk-based authentication that adapts to user behavior and context, bot detection focused on behavioral micro-signals rather than volume alone, device intelligence that persists beyond cookies or IPs, and API-level monitoring that surfaces abnormal access patterns across digital channels.
Targeted multivector account takeovers
Today’s most effective account takeover campaigns rarely rely on a single point of failure. Instead, attackers deliberately chain together multiple techniques such as phishing, SIM swapping, malware and social engineering to exploit gaps between controls that were designed to operate independently.
GenAI has made this coordination easier and detection harder to spot. Messages adapt in real time, social-engineering scripts mirror legitimate communication styles and cloned voices or writing patterns help attackers progress once initial access is gained. In these scenarios, no individual safeguard necessarily breaks. The risk emerges in the handoffs between fraud, identity, mobile authentication and security systems, where fragmented visibility slows recognition of coordinated abuse.
“As takeover tactics become more coordinated, perimeter-based defenses alone aren’t enough,” explains Velikić. “What separates resilient programs from reactive ones is the ability to connect identity, behavioral and transactional signals across the customer journey and act quickly when activity starts to align in suspicious ways.”
According to Velikic, leading financial services organizations are strengthening authentication beyond passwords and SMS-based authentication, continuously reassessing risk throughout an active session, and preserving human judgment for complex edge cases where automation alone may lack the context to distinguish fraud from legitimate customer behavior.
Mule account and transaction laundering networks
Mule networks have evolved from isolated fraud schemes into highly coordinated financial operations. Instead of moving funds through a handful of accounts, modern laundering networks distribute transactions across dozens or hundreds of accounts, platforms and jurisdictions. AI has accelerated this evolution by enabling rapid mule recruitment as well as automated transaction timing and behavior that closely mirrors legitimate customer activity.
For financial institutions, the risk extends well beyond direct financial loss. These networks are designed to exploit gaps between fraud, onboarding and anti-money laundering (AML) controls, creating compliance exposure and weakening an institution’s ability to demonstrate effective oversight under regulatory scrutiny.
“Traditional AML models were built to evaluate transactions one at a time, as they’re happening, or after the fact,” explains Fox. “But mule networks don’t operate in isolation. They move funds through coordinated paths over time, across multiple accounts and platforms. Detecting that activity requires understanding how accounts, devices and transactions connect at scale, and spotting patterns like synchronized timing or repeated routing that only emerge when you look at behavior holistically.”
According to Fox, leading institutions are also bringing onboarding and identity intelligence into transaction monitoring, allowing early risk indicators to be linked to downstream behavior. By unifying fraud, AML and identity signals, teams reduce blind spots and limit the ability of mule networks to move funds undetected across systems and borders.
For many institutions, the real challenge begins after suspicious activity is detected. Identifying risk is one thing — sustaining compliance, audit readiness and operational consistency as volumes rise is another.
For a global money-transfer provider, maintaining regulatory compliance was just as critical as disrupting fraud. The organizations partnered with TELUS Digital to strengthen both. Alongside enhanced monitoring and escalation processes, our teams delivered in-depth sanctions and interdiction training. We also equipped investigators with compliance-focused tools such as standardized workflows, embedded sanctions and watchlist checks, and pre-approved documentation templates to support consistent decisioning and regulatory reporting. TELUS Digital specialists also provided ongoing guidance on complex escalations, reinforced by a disciplined quality-assurance program.
The result was more accurate escalation of high-risk activity, consistently stronger audit performance (97%+) and reduced exposure to laundering risk, all while allowing legitimate customer transactions to continue without unnecessary friction.

Financial crime and compliance maturity assessment
Open banking and application programming interfaces (API) exploitation
Open banking has fundamentally changed how financial services operate. By design, APIs now sit at the center of customer data sharing, payments initiation and third-party innovation. For leaders, this has shifted risk away from customer-facing interfaces and into the system-to-system connections that power modern financial ecosystems.
Attackers have been quick to capitalize on this evolution. APIs are attractive precisely because they operate behind the user interface, connect trusted systems and often execute at machine speed. When authentication controls are weak, permissions are overly broad or monitoring is limited, a single compromised endpoint can expose large volumes of sensitive data or enable unauthorized transactions without triggering traditional fraud alerts. These attacks don’t look like fraud in the conventional sense. They unfold quietly inside trusted workflows, making them harder to detect and faster to scale.
Rather than relying on static controls alone, financial institutions are increasingly treating APIs as high-risk assets that require continuous validation. Effective defense combines real-time visibility into API behavior, strict least-privilege access and zero-trust assumptions, with ongoing testing designed to mirror how attackers actually probe for weaknesses. The goal is not just to secure APIs at launch, but to continually pressure-test them as integrations, permissions and AI-driven services evolve.
This is where adversarial testing platforms are gaining traction. For example, TELUS Digital’s Fuel iX Fortify enables teams to simulate real-world attack techniques against APIs and GenAI components at scale, uncovering misconfigurations, credential-abuse paths and privilege-escalation risks before they can be exploited. By automating this testing, organizations can significantly reduce evaluation time and cost, while enabling both technical and non-technical teams to participate in API risk assessment — an important advantage as open-banking ecosystems continue to expand.
Crypto, decentralized finance (DeFi) and virtual asset fraud
Crypto-related risk rarely looks like a single, obvious fraud event. Instead, it tends to emerge at the edges of the ecosystem, where visibility is limited and accountability is distributed across wallets, protocols and platforms outside of traditional banking infrastructure.
As crypto and DeFi adoption expands, fraudsters are exploiting the speed, irreversibility and cross-border nature of blockchain transactions to move illicit funds quickly. Assets can be routed through chains of wallets, obscured via mixers or bridges, or embedded within seemingly legitimate DeFi activity before compliance teams can intervene. When weaknesses exist in smart contracts or protocol governance, value can be drained at scale in minutes, leaving little opportunity for recovery.
“What we’re seeing in virtual-asset fraud is a collapse of the time window institutions traditionally rely on,” says Fox. “By the time a transaction looks suspicious, the funds have already moved, often multiple times. That reality pushes teams toward earlier, proactive risk assessment rather than post-event investigation.”
In response, leading organizations are extending fraud and AML capabilities into crypto environments instead of treating them as siloed domains, Fox explains. This includes using blockchain intelligence to assess wallet-level risk, trace transaction paths tied to known criminal activity and surface exposure earlier, before losses compound across platforms.
“What we see consistently is that crypto fraud doesn’t replace traditional financial crime, it complements it,” notes Fox. “The same networks abusing accounts and mule structures in banking are now using blockchain rails to move value faster and with fewer checkpoints. Institutions that treat crypto risk as disconnected from their broader fraud strategy are the ones left reacting after losses occur.”
Institutions are also paying closer attention to the DeFi platforms and smart contracts they interact with, recognizing that weaknesses at the protocol level can translate directly into financial and reputational risk. By monitoring on-chain behavior, teams can spot early warning signs such as sudden spikes in transfers, unusual routing paths or concentrated movement of funds that deviates from normal usage patterns.
Keeping pace with AI-driven fraud
Across industries, fraud prevention is rising on the leadership agenda as threats grow more sophisticated and harder to contain. In TELUS Digital's Safety in Numbers: Trust and Safety Trends, 2025 report, 69% of surveyed enterprise leaders say fraud detection has become a higher priority this year, and 66% plan to expand investment over the next 12 months.
For financial services organizations, this broader shift intersects with a uniquely complex operating environment. Decades-old core systems now operate alongside cloud platforms, digital channels and a growing ecosystem of fintech and third-party integrations. These layered architectures were not designed to share data seamlessly, limiting real-time visibility across channels and slowing response when attacks unfold in seconds. A coordinated fraud campaign may touch payments, onboarding and customer accounts simultaneously, yet signals are often scattered across separate tools and teams.
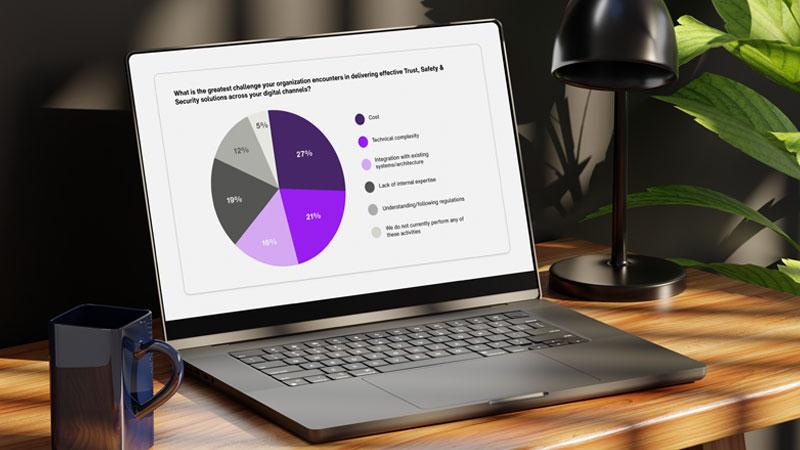
Operational constraints compound the challenge. Strict data-governance and privacy requirements shape what information can be analyzed and how quickly, narrowing the detection window for AI-driven anomalies. At the same time, talent shortages persist. In the aforementioned survey, 16% of enterprise leaders cited lack of internal expertise as a major barrier in delivering effective trust and safety solutions, reflecting the scarcity of specialists trained in AI governance, advanced identity verification and deception-driven fraud detection. Budget constraints, rising compliance expectations and the effort required to manage increasingly interconnected third-party and cloud ecosystems place even more pressure on already stretched fraud and security teams.
Collectively, these factors have created an uneven playing field where adversaries are evolving faster than many institutions can modernize. Keeping pace with deepfake-enabled fraud now requires more than incremental tooling upgrades. It calls for coordinated strategies, specialized expertise and partners who understand both the technical realities of AI-driven threats and the regulatory, operational and customer-experience demands unique to financial services.
Strengthening digital trust in the new era of fraud
Strengthening digital trust in the new era of fraud isn’t just about better tech — it’s about creating a resilient foundation where your institution can grow while minimizing risk. Bridge the gap between advanced AI and human intuition and you move beyond reactive defense to proactive protection. Whether you are navigating the complexities of KYC, KYB and AML or scaling across global markets, you need a partner that integrates seamlessly into your existing governance to enable more informed decision-making in high-stakes environments.
To help you outpace increasingly sophisticated adversaries, our human‑AI hybrid approach provides a decisive edge. By leveraging the Fuel iX Fortify platform alongside our managed compliance operations, you can stress-test AI systems and neutralize deception-driven attacks before they impact your bottom line. This approach is reinforced through strategic technology partnerships with leading providers like Sumsub, which supports full-cycle identity verification, as well as Crowdstrike and CyberArk, which strengthen cyber and AI security across endpoints and privileged access. Together, these capabilities support end-to-end financial crime programs spanning identity verification, onboarding, transaction monitoring, investigations and regulatory reporting.
With TELUS Digital, you also gain the scale and operational maturity required to execute these programs with absolute reliability. With delivery operations spanning 35 countries and support in over 50 languages, we help you maintain regulatory confidence while scaling protection across every payment and customer interaction. Our compliant delivery environments and experienced teams integrate seamlessly with your existing infrastructure, strengthening your controls without ever compromising the speed or quality of your customer experience. If you’re ready to accelerate your defenses with a partner that understands the regulatory, operational and human realities of modern financial crime, our team is here to help.